Features
PowerShell Pro Tools provides functionality to enhance PowerShell development, build GUIs and increase desktop productivity.
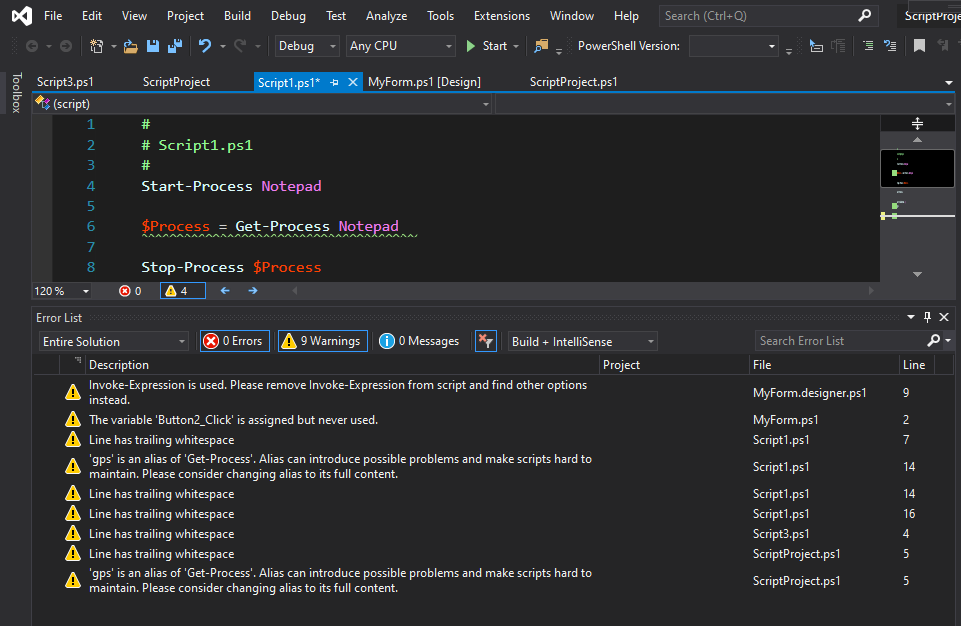
 PowerShell Tools for Visual Studio
PowerShell Tools for Visual Studio
Edit, debug, compile and organize scripts in Visual Studio.
Don't own Visual Studio? PowerShell Pro Tools works with Visual Studio Community Edition.
 PowerShell Pro Tools for Visual Studio
Code
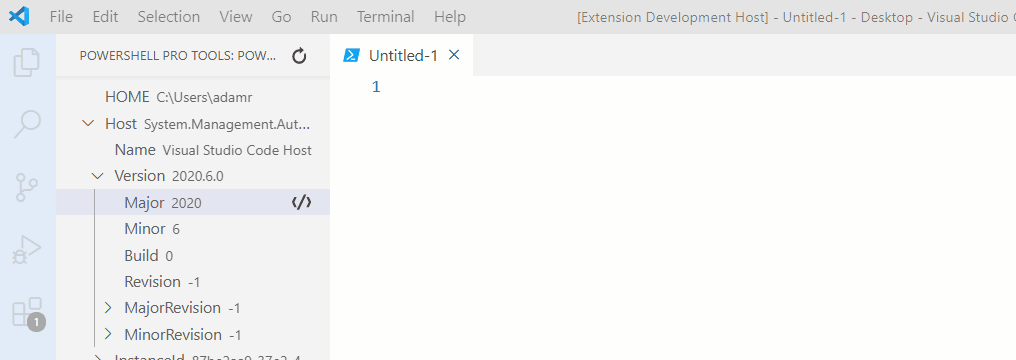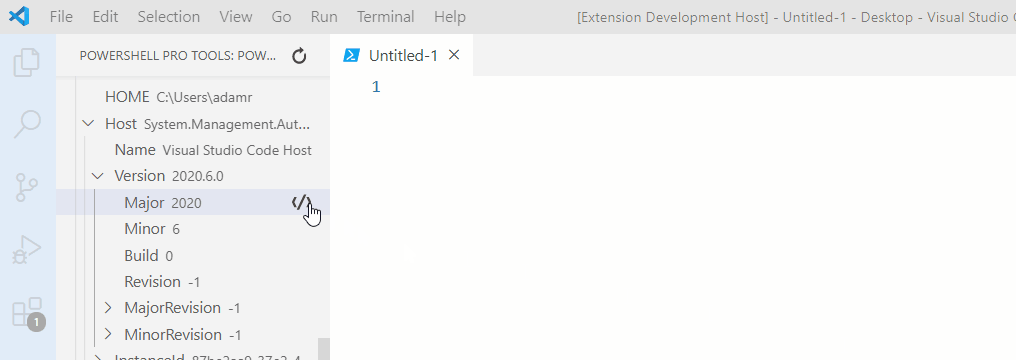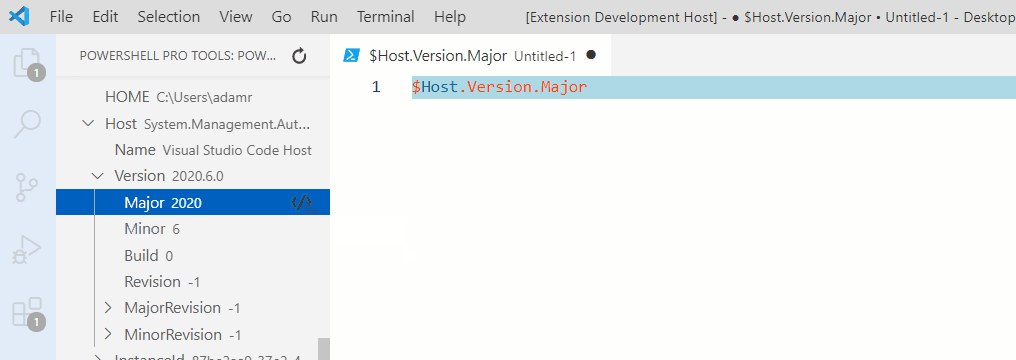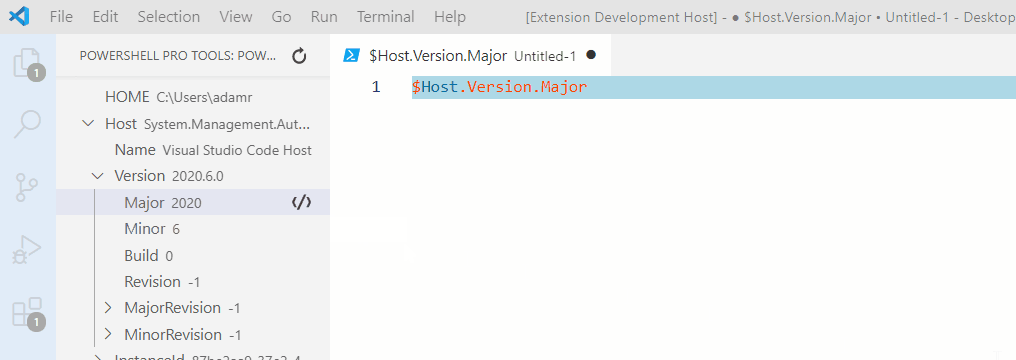
PowerShell Pro Tools for Visual Studio
Code
Enhancements and tools for working with PowerShell in Visual Studio Code.
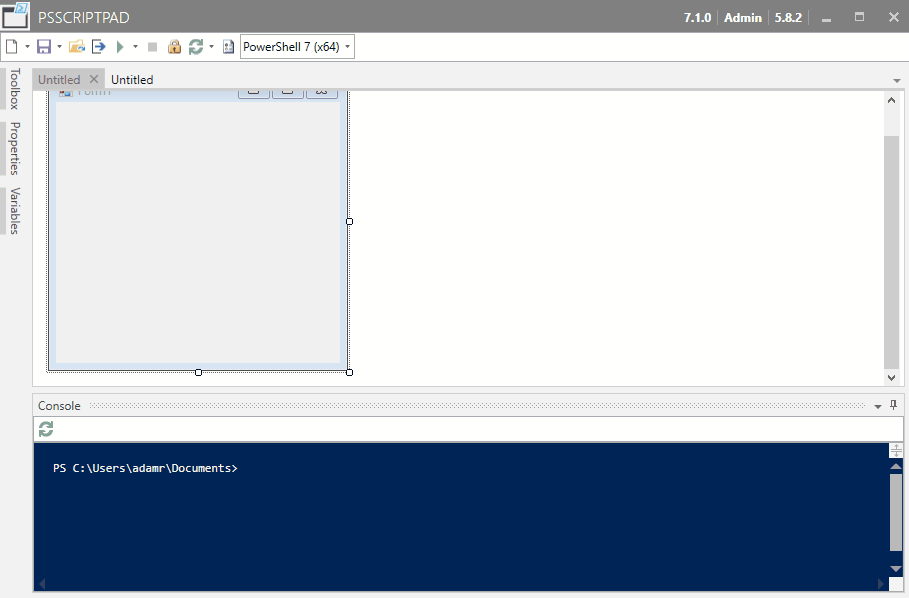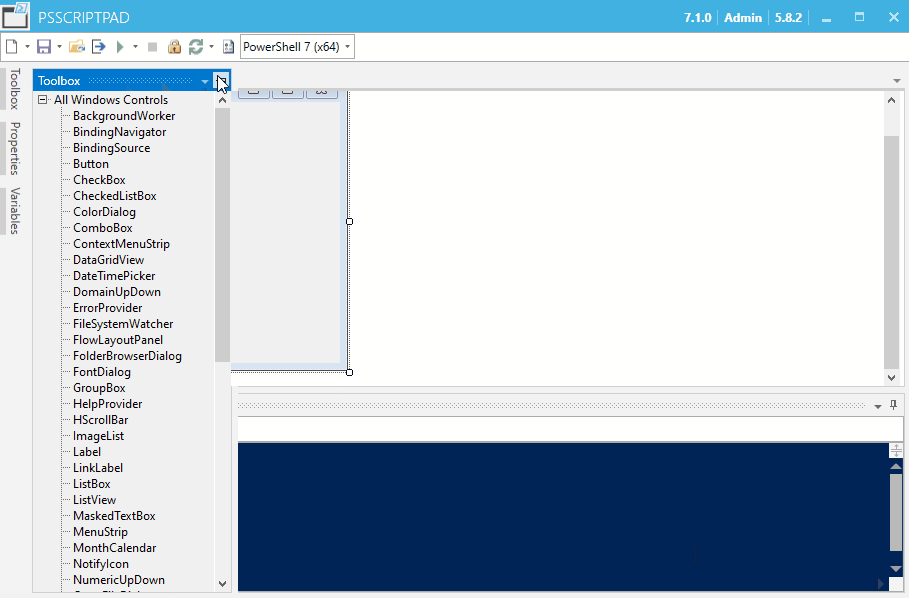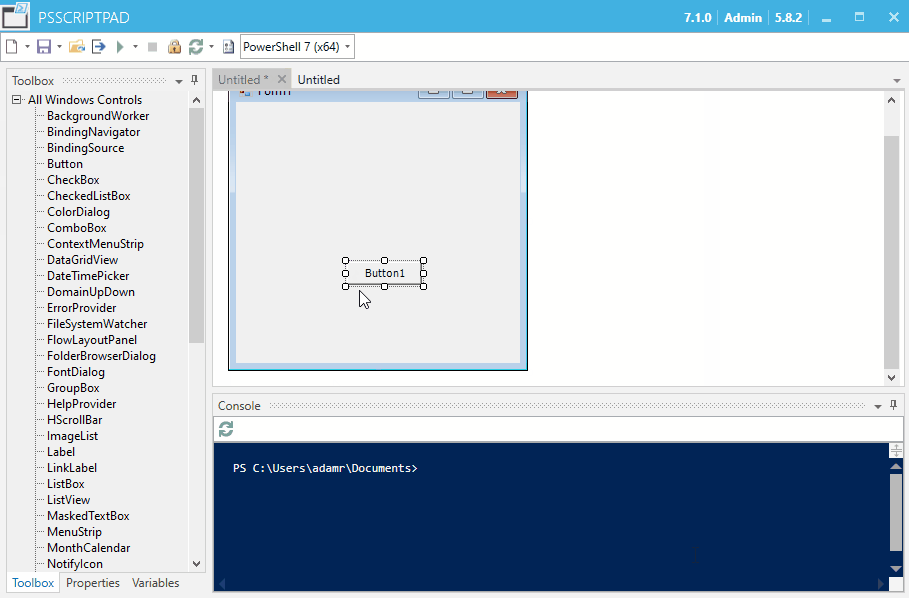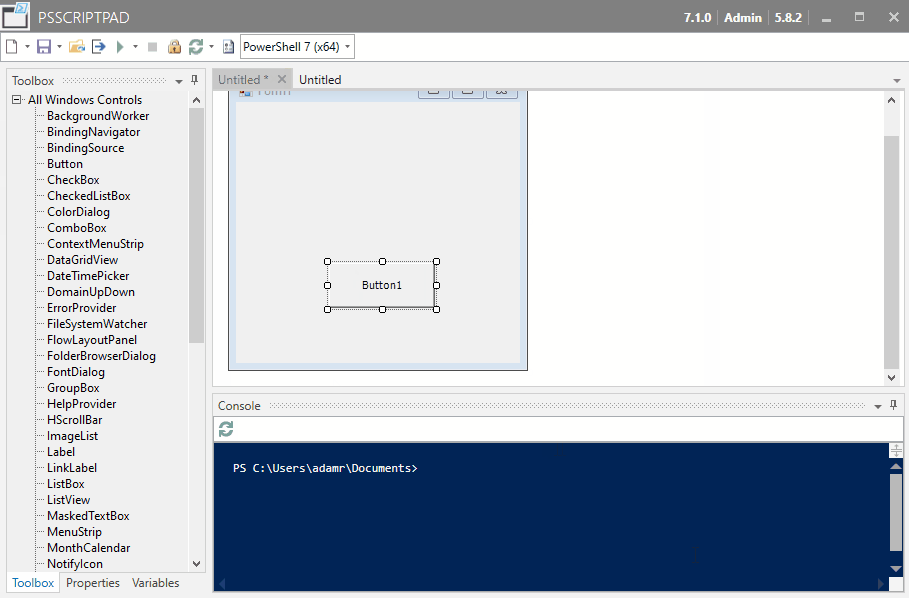
PSScriptPad
The single-file PowerShell IDE with editing, debugging, form designers and packaging.
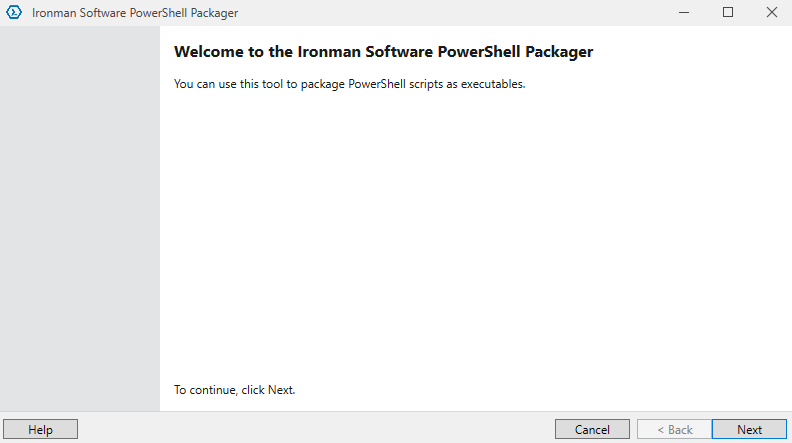
PowerShell Packager
Package PowerShell scripts as executables.
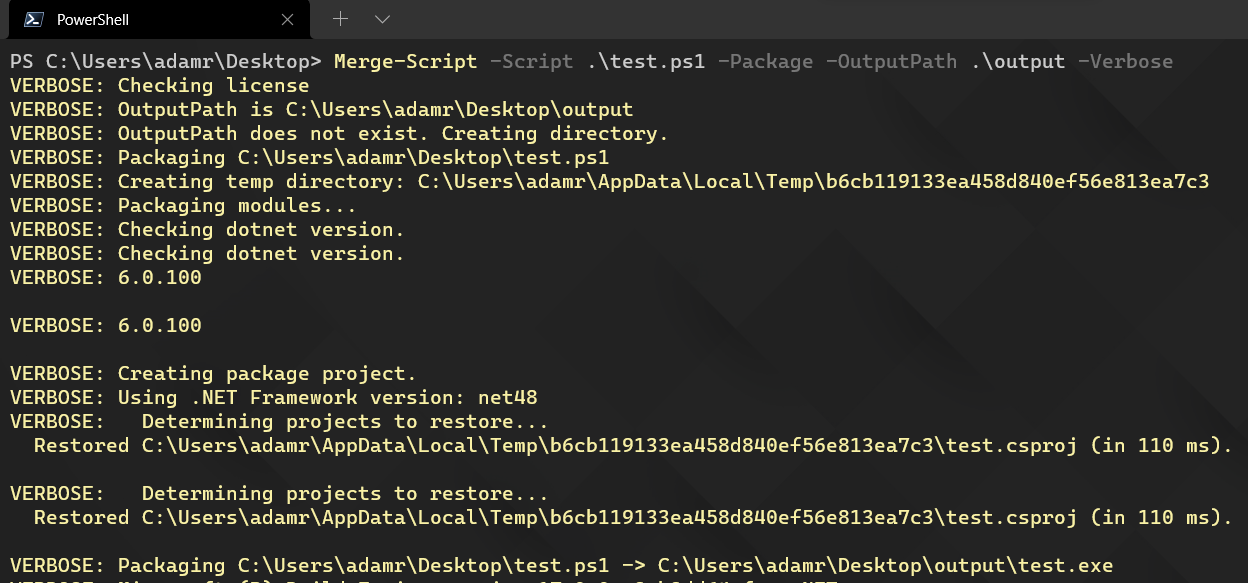
Module
Command line tools to package scripts and create installers.